搜索结果: 1-15 共查到“Resistant”相关记录342条 . 查询时间(0.156 秒)
Abietic acid encapsulated Sn-57Bi alloy nanoparticles as oxidation resistant solder material
Sn-57Bi alloy nanoparticles abietic acid encapsulation metal oxide reduction
2023/12/21
Low-melting point solder Sn-57Bi alloy nanoparticles were synthesized and encapsulated with abietic acid (aa) thin layer to form a core-shell structure. Formation of nanoparticle enhances its mechanic...

A novel combination therapy for treating vancomycin-resistant bacterial infections(图)
万古霉素 耐药细菌感染 联合疗法
2023/6/5
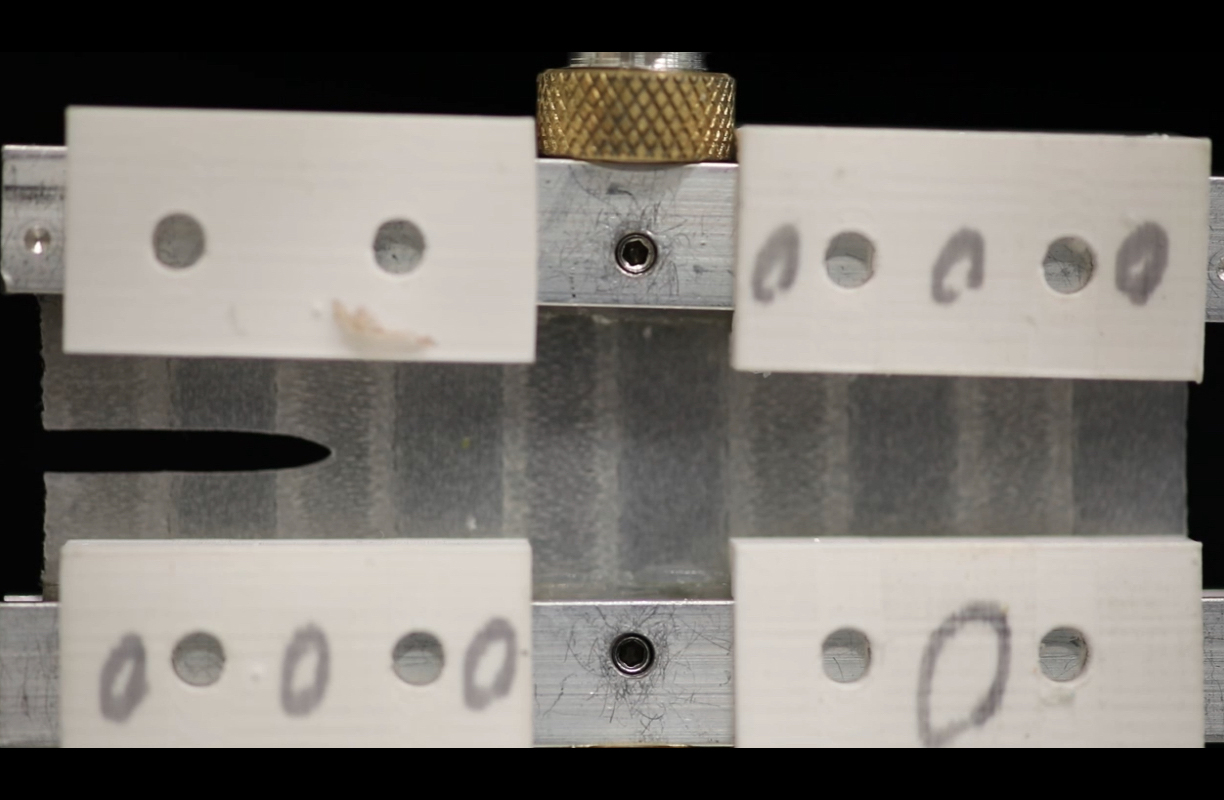
Inspired by the human heart, Penn Engineers design tear-resistant soft material(图)
抗撕裂软材料 人类心脏 机器人
2023/7/7
Drug-resistant bacteria found in the guts of lemurs who live around humans The more human interaction they had, the higher the proportion of resistant bugs
antibiotics resistance lemur gut microbiota
2021/8/10
Researchers have found evidence for antibiotic resistance in the gut microbiomes of lemurs living close to humans. The more human contact they have, the more antibiotic resistance there is. Even capti...

Can bacteria make better crack-resistant materials?(图)
bacteria better crack-resistant materials
2021/3/12
Biological systems can harness living cells for growth and regeneration, but engineering systems cannot -- or couldn't until now.Qiming Wang and other researchers at the University of Southern Ca...

New way to identify disease-resistant genes in chocolate-producing trees(图)
New way disease-resistant genes chocolate-producing trees
2019/12/13
Chocolate-producing cacao trees that are resistant to a major pathogen were identified by an international team of plant geneticists. The NSF-funded finding points the way for plant breeders to develo...
Subversion-Resistant Commitment Schemes: Definitions and Constructions
Commitment schemes subversion security common reference string model
2019/9/23
A commitment scheme allows a committer to create a commitment to a secret value, and later may open and reveal the secret value in a verifiable manner. In the common reference string model, commitment...
Ci-Lock: Cipher Induced Logic Locking Resistant Against SAT Attacks
Logic locking Block cipher Hardware obfuscation
2019/8/30
Protection of intellectual property (IP) cores is one of the most practical security concern for modern integrated circuit (IC) industry. Albeit being well-studied from a practical perspective, the pr...
Collusion Resistant Trace-and-Revoke for Arbitrary Identities from Standard Assumptions
public-key cryptography traitor tracing, revocation
2019/8/30
A traitor tracing scheme is a multi-user public-key encryption scheme where each user in the system holds a decryption key that is associated with the user's identity. Using the public key, a content ...
CCM-SIV: Single-PRF Nonce-Misuse-Resistant Authenticated Encryption
AEAD AES-GCM AES-GCM-SIV
2019/8/6
We propose a new nonce-misuse-resistant authenticated encryption scheme, which instantiates the SIV paradigm of Rogaway and Shrimpton. In contrast to the GCM-SIV approach proposed by Gueron and Lindel...
Athena: A verifiable, coercion-resistant voting system with linear complexity
cryptographic protocols election schemes
2019/7/8
Seminal work by Juels, Catalano & Jakobsson delivered a verifiable, coercion-resistant voting system with quadratic complexity. This manuscript attempts to advance the state-of-the-art by delivering a...
On the Complexity of Collision Resistant Hash Functions: New and Old Black-Box Separations
Collision Resistance Statistical Zero Knowledge Black box separations
2019/6/12
The complexity of collision-resistant hash functions has been long studied in the theory of cryptography. While we often think about them as a Minicrypt primitive, black-box separations demonstrate th...
Collusion Resistant Broadcast and Trace from Positional Witness Encryption
Witness Encryption Trace and Revoke Broadcast Encryption
2019/1/18
An emerging trend is for researchers to identify cryptography primitives for which feasibility was first established under obfuscation and then move the realization to a different setting. In this wor...
A CCA-secure collusion-resistant Identity-based Proxy Re-encryption Scheme
Identity-Based Proxy Re-Encryption Collusion-resistance Random Oracle
2018/11/29
Cloud storage enables its users to store confidential information as encrypted files in the cloud. A cloud user (say Alice) can share her encrypted files with another user (say Bob) by availing proxy ...
Data Oblivious ISA Extensions for Side Channel-Resistant and High Performance Computing
Data oblivious computing constant time computing secure hardware
2018/11/19
Blocking microarchitectural (digital) side channels is one of the most pressing challenges in hardware security today. Recently, there has been a surge of effort that attempts to block these leakages ...


