搜索结果: 1-15 共查到“Q-algebra”相关记录270条 . 查询时间(0.078 秒)
Academy of Mathematics and Systems Science, CAS Colloquia & Seminars:The Cohen-Macaulay Auslander algebra of string algebras
串代数 Cohen—Macaulay—Auslander代数 拓扑 同调
2023/11/13
We introduce a general framework encompassing the main hard problems emerging in lattice-based cryptography, which naturally includes the recently proposed Mersenne prime cryptosystem, but also code-b...
New Protocols for Secure Linear Algebra: Pivoting-Free Elimination and Fast Block-Recursive Matrix Decomposition
secure linear algebra multiparty computation
2018/8/2
Cramer and Damgård were the first to propose a constant-rounds protocol for securely solving a linear system of unknown rank over a finite field in multiparty computation (MPC). For mm linear equ...
MRHS Solver Based on Linear Algebra and Exhaustive Search
Algebraic cryptanalysis MRHS LowMC
2018/1/31
We show how to build a binary matrix from the MRHS representation of a symmetric-key cipher. The matrix contains the cipher represented as an equation system and can be used to assess a cipher's resis...
The program opens with four days of tutorials that will provide an introduction to major themes of the entire program and the four workshops.The goal is to build a foundation for the participants of t...
第一届冬季数学高级研讨会(First Winter Workshop on Advanced Topics in Mathematics:Commutative Algebra and Banach Space Theory)
第一届 冬季数学 高级研讨会
2017/12/20
This four-day workshop is devoted to discuss advanced topics from commutative algebra and Banach space theory. The theme of this workshop is twofold: parallel series of lectures will be delivered in c...
Linear algebra is an important area of mathematics and it is at the heart of many scientific, engineering, and industrial applications. Research and development in linear algebra include theoretical s...
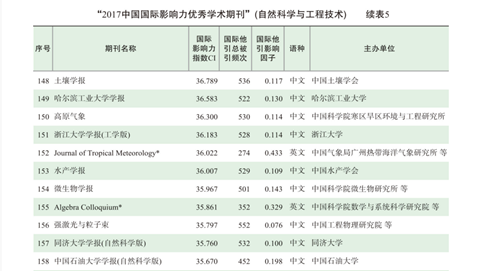
日前,由中国期刊协会、中国科学技术期刊编辑学会、中国高校科技期刊研究会、全国高等学校文科学报研究会、《中国学术期刊(光盘版)》电子杂志社有限责任公司5家单位联合主办,同方知网承办的“2017中国学术期刊未来论坛”在北京会议中心隆重举行。此次会议中,中国学术期刊(光盘版)电子杂志社有限责任公司和清华大学图书馆联合发布了《2017中国学术期刊国际引证年报》,公布了备受学术界关注的2017年度“中国最具...
2017年国际代数,离散数学和应用会议(International Conference on Algebra,Discrete Mathematics,and Applications)
2017年 国际代数,离散数学和应用 会议
2017/11/24
Fields Medal is considered as the Nobel Prize in Mathematics. We are pleased to announce that Fields Medalist Prof. E. Zelmanov is delivering Plenary Lecture in the conference.The purpose of the confe...
Solving Multivariate Polynomial Systems and an Invariant from Commutative Algebra
post-quantum cryptography multivariate cryptography Groebner basis
2017/6/22
The security of several post-quantum cryptosystems is based on the assumption that solving a system of multivariate (quadratic) polynomial equations p1=⋯=pm=0p1=⋯=pm=0 over a finite field ...
The proportion of students taking a first algebra course in middle school has doubled over the past generation and there have been calls to make eighth grade algebra universal. We use significant poli...
Octonion Algebra and Noise-Free Fully Homomorphic Encryption (FHE) Schemes
secret-key cryptography FHE
2016/1/27
Brakerski showed that linearly decryptable fully homomorphic encryption
(FHE) schemes cannot be secure in the chosen plaintext attack (CPA)
model. In this paper, we show that linearly decryptable FH...
Differentially Private Linear Algebra in the Streaming Model
Differential Privacy Linear Algebra Random Projection
2016/1/7
The focus of this paper is a systematic study of differential privacy on streaming data using sketchbased
algorithms. Previous works, like Dwork et al. (ICS 2010, STOC 2010), explored random sampling...
Analysis of a key exchange protocol based on tropical matrix algebra
Tropical algebra cryptography key-exchange
2015/12/23
In this paper we consider a two party key-exchange protocol
proposed in [4, Section 2] which uses tropical matrix algebra as a
platform. Our analysis shows that the scheme is not secure.
Nearly Sparse Linear Algebra
Sparse Linear Algebra Block Wiedemann Algorithm Discrete Logarithm
2015/12/22
In this article, we propose a method to perform linear algebra
on a matrix with nearly sparse properties. More precisely, although
we require the main part of the matrix to be sparse, we allow some ...


